In LLM functions, a take a look at may ensure that including more context to a question-answering prompt results in more accurate and relevant answers. Conducting E2E checks reduces the chance of deployment failures and ensures efficient manufacturing syntax testing operation. It’s important to maintain the assertion section not brittle, the goal of the combination check is to ensure the pipeline is smart, not that it’s right. While element tests provide a targeted view, a broader perspective is sometimes essential. Integration exams evaluate the cooperation between totally different modules, ensuring they function collectively seamlessly. Always start with organising the CI workflow, as it’s easy and reduces the barrier to testing.
Metamorphic Testing Invariance Exams
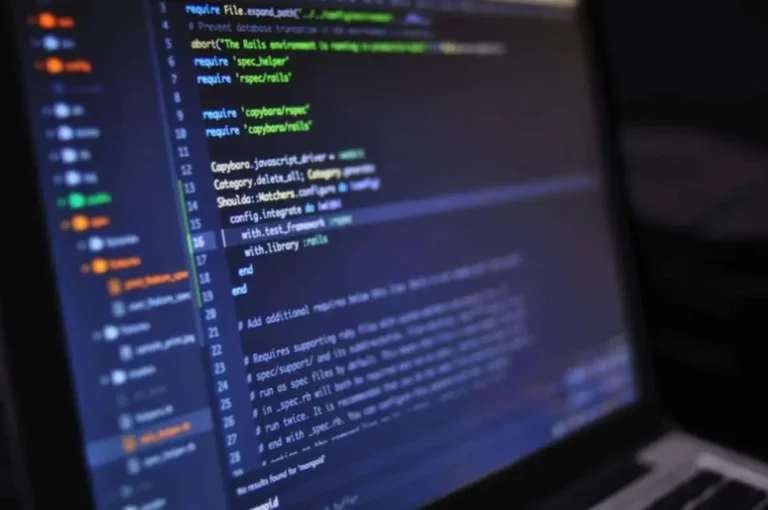
The main objective of syntax testing is to guarantee that the code is written in a method that is consistent with the programming language’s syntax rules. Syntax testing includes analyzing the code to determine errors in the syntax, corresponding to incorrect use of punctuation, missing or additional brackets, and incorrect use of keywords. Non-functional testing refers to aspects of the software program that is most likely not related to a selected operate or person action, corresponding to scalability or other efficiency, conduct beneath certain constraints, or safety. Testing will decide the breaking point, the point at which extremes of scalability or efficiency results in unstable execution.
Domain 6: Safety Evaluation And Testing (designing, Performing, And Analyzing Security Testing)
Black-box testing offers the tester no inside particulars; the software is handled as a black field that receives inputs. In software program testing, various strategies corresponding to unit tests, property-based testing, component exams, and integration tests every have their very own strengths and weaknesses. Black box testing is a testing technique during which the internal workings of the software aren’t identified to the tester. Whereas, White box testing is a testing approach in which the tester has knowledge of the interior workings of the software program, and may test individual code snippets, algorithms and strategies.
Creating Secure AspWeb Functions
Today I’m going to put in writing about unit testing, to be actual unit testing in your Prometheus Alert Rules. Design Test circumstances should be chosen randomly from the input domain of the element based on the enter distribution. Syntax-Driven Testing – This type of testing is utilized to strategies that could be syntactically represented by some language. The precise artifacts produced are an element of the software program development model used, stakeholder and organisational wants. Agile software growth generally involves testing whereas the code is being written and organizing groups with each programmers and testers and with group members performing each programming and testing. Functional testing refers to activities that verify a specific motion or operate of the code.
What Can Be Recognized By Black Field Testing
We will discover all of the testing choices by starting with an instance from the Titanic dataset, the place we calculate get_family_size, the place family dimension is predicated on the number of mother and father and siblings. This easy information gives you an overview of what Black Box Testing is all about and why it matters in software growth. The two be a half of strategies in MapReduce are Reduce facet or Repartition be part of and Map-side join.
Syntax Testing: The Grammar Verify Of Your Programming Code
Hashes are also effective at disguising knowledge to make it less weak to guessing assaults. An attacker wanted simply to make use of smart guessing ways to realize entry to this information. Instead, using a filename based mostly on a hash would make it unpredictable and would use a big enough key area to stop guessing. Syntax checking is the ultimate defense mechanism in opposition to malicious enter in pc methods.
- Code that’s free from syntax errors is simpler to take care of as a outcome of it’s simpler to learn and understand.
- Security testing is important for software program that processes confidential data to stop system intrusion by hackers.
- The phrases load testing, performance testing, scalability testing, and quantity testing, are often used interchangeably.
Black Box Testing is an important technique in software testing that focuses on evaluating the software’s functionality from the user’s perspective with out considering its inside workings. By using strategies like practical testing , regression testing , and non-functional testing , this strategy ensures the software meets its necessities and specifications. It helps determine points associated to performance, efficiency, and usability, making it a vital practice in software program growth . Despite some limitations, corresponding to potential repetitive testing and difficulties with complex inputs, Black Box Testing stays a priceless software for delivering high-quality, user-friendly software.
In addition to this, you should also specify a character encoding set in your Web pages. Enforcing a selected character set limits which characters are legitimate for your website and eliminates the paradox that hackers might exploit by using different character sets. Accumulating huge quantities of security test results is easy; really bettering safety primarily based on those outcomes is far more tough. An instance of this is organizations performing vulnerability scans on an almost steady basis.
Further validation and analysis on bigger datasets are needed to ensure the model delivers real value and performs nicely in production within the following part. One main good thing about syntax testing comes from the reassurance that there aren’t any misunderstandings about what are authorized data and what’s not. When a formal syntax description is written out, such issues will floor even before the testing begins. This is one other instance during which the method of designing and creating test cases helps to forestall errors. Ideally, the formal syntax should be used to specify the system in the first place. The functions and limitations specified above may prove useful to undertake syntax testing.
Describe fundamental security guidelines including the need for a safety coverage, process, training and the need to audit, patch and securely configure techniques. It supplies an exposition of IR fashions, devices, cross-language IR, parallel IR, and integrating textual content with structured information. Belew (2001) presents a cognitive science perspective to the analysis of information as a computer science self-discipline utilizing the notion Finding Out About. Implement Process Rights Management along with describing PRM, course of privileges, determining rights required by course of, profiling privileges utilized by processes, and assigning minimal rights to a course of. AnalysisRandom Testing uses such model of the input domain of the part that characterizes the set of all possible input values.
Nevertheless, running some partial implementation of the software program or a prototype of any sort (dynamic testing) and obtaining positive feedback from them, can additional increase the certainty that the SRS is appropriately formulated. Software design has traditionally targeted on growing code to supply desired or required functionality. While safety requirements may properly be outlined for an utility in development, they are hardly ever required to achieve the specified targets for the application’s design.

Figures 5.12 (C#) and 5.13 (VB.NET) show how to use an everyday expression to examine for these patterns. Though amateurish software can nonetheless be broken by this sort of testing, it’s unusual for professionally created software program right now. However, the myth of the effectiveness of the wily hacker doing dirty things on the keyboard persists within the public’s thoughts and in the minds of many who are uneducated in testing experience. Another caveat is that syntax testing might lead to false confidence, a lot akin to the means in which monkey testing does.
But sample matching is greater than blocking and permitting individual characters. For example, consider a Web software that saves information to a file, and selects the filename primarily based on person enter. To forestall listing traversal or file entry assaults, you might permit users to input solely alphanumeric knowledge, which you’ll enforce with an everyday expression. But what occurs if the user selects a filename using a reserved DOS system name corresponding to COM1, PRN, or NUL? Although these device names don’t comprise something apart from alphabetic characters, accessing these devices would possibly cause a denial of service or facilitate some other kind of attack. For some kinds of input you want to enable only identified good data after which carry out a follow-up check to ensure that enter doesn’t comprise identified dangerous knowledge.